tl;dr : Google documents leak full name and e-mail address via ClickJacking the “request permissions” dialog in a private doc.
Details:
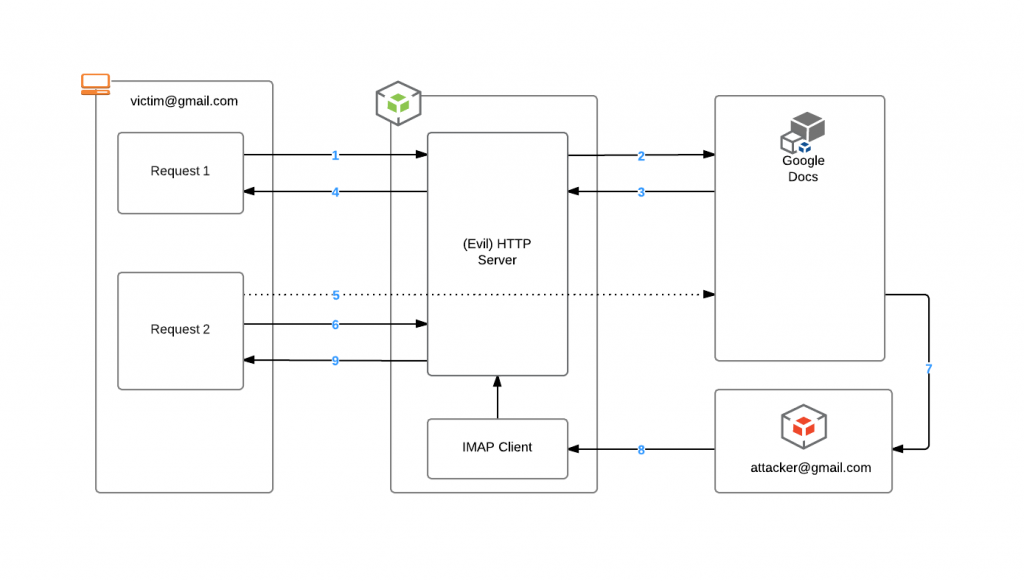
- Victim visits the evil site.
- The evil server uses the google docs API to creates a unique document for the visitor.
- The document is named with the unique session id of the victim.
- The document is set to private.
- A URL to the new document is returned to the server.
- An iframe is created with the following page from google:
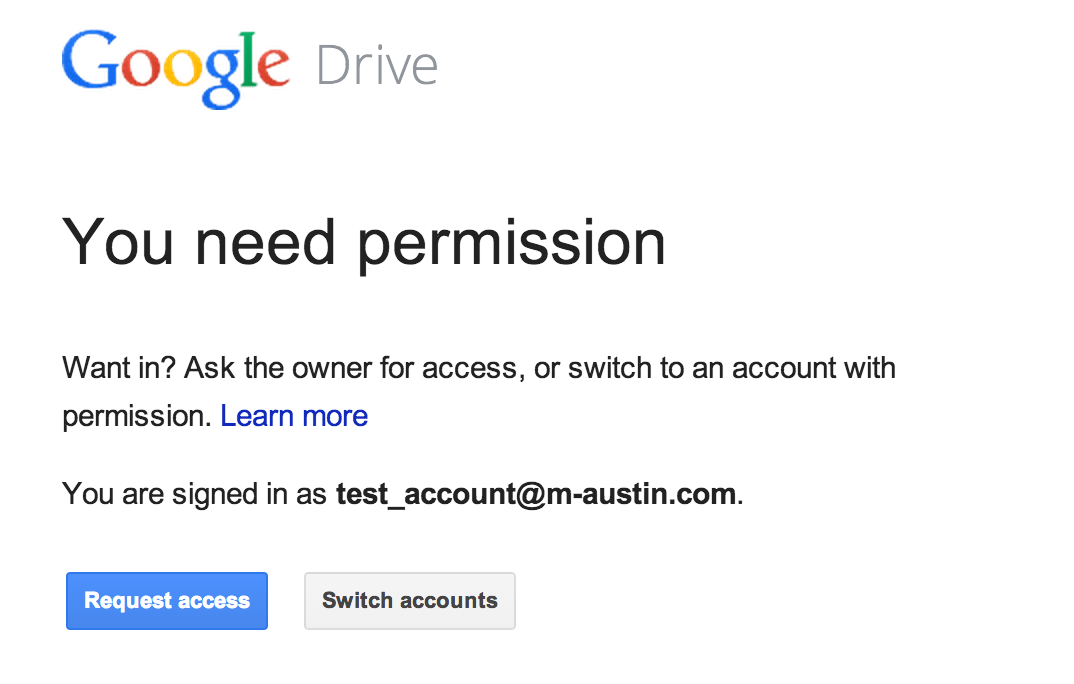
- This page is cropped to only have the “request access button”.
- Style is used to make the iframe 100% transparent and always on top of the page. Javascript is used to make the cropped request access button follow the mouse around the page.The resulting “Click Jack” or UI Redressing would look like:
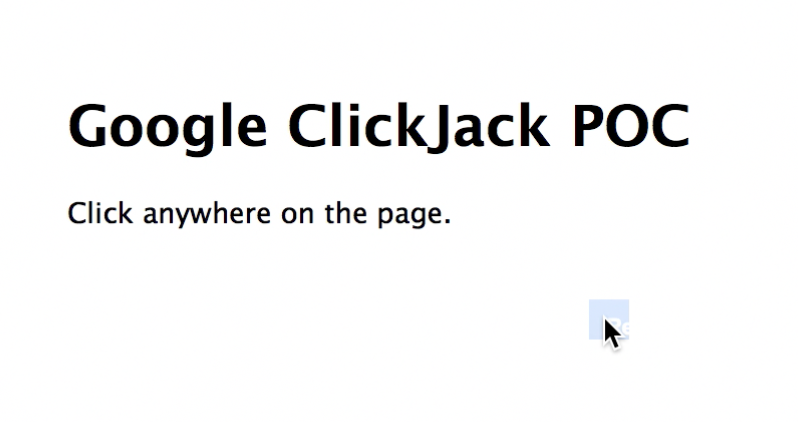
- When the user clicks anywhere on the evil page they are actually clicking on the “request access” button. of the google doc.
- Once the user clicks on the link the page starts polling with ajax for an update from the server.
- Google sends an e-mail, on behalf of the user including full name and e-mail, to the creator of the document ([email protected]) to request access.
- The evil server is running an IMAP client listening for document requests to [email protected].
- The IMAP client receives the request from the google doc that is named after the value of the session key. The evil server can now tie the user session (from the document requesting title) to the “from: ” name and address in the request. The polling request from step 6 will be updated with the identity of the current user.
Success!!!